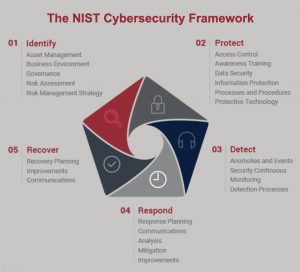
Florida cities, Riviera Beach, Lake City and Village of Key Biscayne, all came under siege by what appears to be an organized barrage of cyber attacks. Organizations should all begin to pay close attention to email traffic, network anomalies and users cyber habits at work and at home. Awareness and training are the first line of defense.

(Click the pic for article)